Odds are, in the last few years you have received a spam text or email supposedly from reputable companies such as Apple and Amazon. These texts or emails were probably claiming you owed them a certain amount or that there was an issue with your account that could all be solved if you clicked on the very suspicious link they included.
These tricks have become fairly well known and easy to spot. The messages often contain misspellings or odd grammar, the URLs and links they provided only vaguely resembled the actual company they claimed to be from, and should you dare to click on the link, the website would most likely look a little off. For many, these texts were probably easy to spot as fake, delete, and move on from. No big deal.
Text scams are on the rise
Yet, despite the shortcomings in these earlier iterations of the scam, many still fell for them. The number of times I received a panicked call from my parents or grandparents because they were worried they somehow owed Apple $537.19 and weren’t sure how it could have happened and could I please help them look at their Apple transactions, is more than one might like to think. Even my younger more tech-savvy friends have fallen—or nearly fallen—prey to such scams.
In fact, according to the Federal Trade Commission, from July 2020 to June 2021, Amazon scammers alone had increased more than fivefold and managed to steal over $27 million from Americans.
These scams are not limited to Amazon either. Often, these bad actors will pose as the victim’s bank or credit union and lead them to a copy of your online banking website to trick them into sharing their credentials. While this trick is not exactly “new,” the method and execution behind it have reached a near-perfect level.
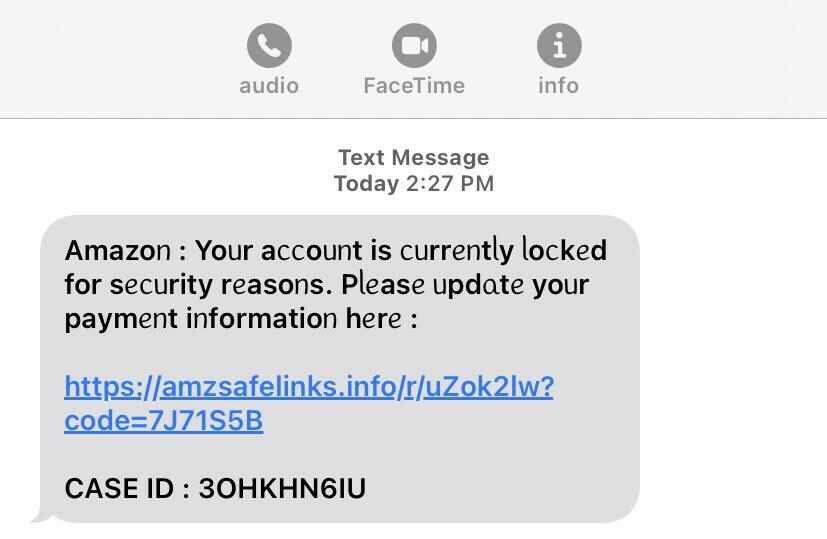
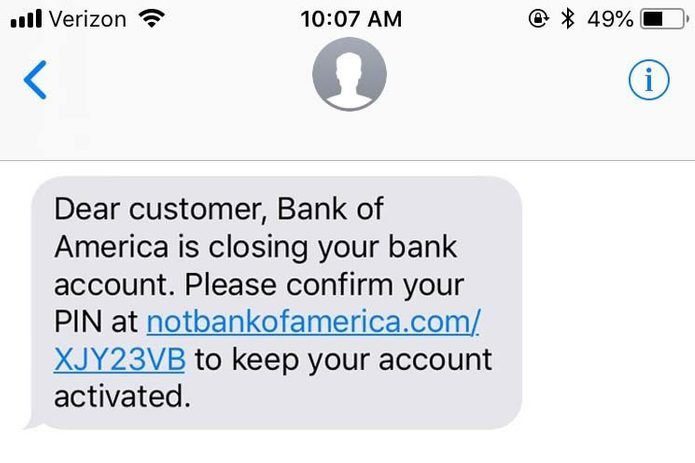
The original form of the scam became popular around 2020 and looked a little something like this:
Here, you can see pretty obvious clues that these messages are fake. The inconsistent font and style in the first one is a clear giveaway, along with the random string of numbers and letters included in both URLs and in the second image, the URL clearly states it is in fact “not” the Bank of America.
Of course, scammers hope that anyone reading these messages would instantly panic at the idea of their bank account suddenly being shut down, and click on the link so quickly they don’t notice these disparities. But while these scams managed to be slightly successful, they rarely fooled anyone paying close attention. And as consumers have been working to better spot these scams, bad actors have worked even harder to improve their game.
Homograph attacks
Now, instead of providing a URL that is off by a letter or two or includes a handful of random letters or numbers before or after the main URL, scammers instead provide an indiscernible forgery of the URL that brings victims to another seemingly exact copy of the website in what’s called a Homograph Attack. But how are they doing this?
In a Homograph Attack, fraudsters replace one or two letters in a URL with letters from another alphabet—mainly the Cyrillic (Russian) alphabet. Typically, they swap out the “a” or insert a capital “I” in place of a lowercase “l.” In some mediums, these small changes can be easier to spot, but overall, they are usually much more difficult to find.
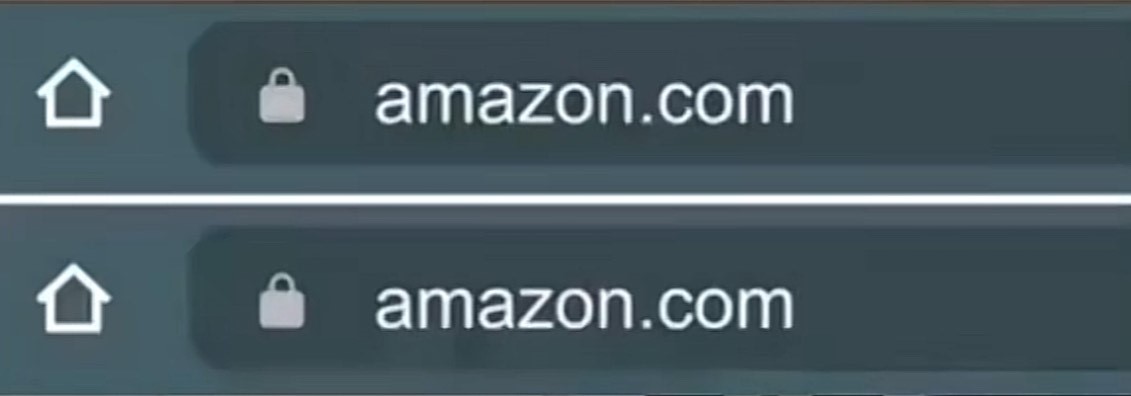
Take a look at the example to the right. One is the actual amazon.com URL and the other is a fake URL which would lead users to a copy of the real site. Can you tell which is which?
Spoiler: the top one is the real amazon.com address, while the second is the scam site. The second “a” in the lower web address is actually a Cyrillic “a.” Depending on the web browser or phone you’re using, these fake addresses can look identical to the real ones and be nearly impossible to spot!
KnowledgeFlow Cybersafety Foundation provided a few more examples of just how convincing these URLs can be:


Telling facts from font
So how can you spot the difference between these identical addresses and how can you help your members to do the same? The best ways to prevent your members from falling prey to these scams are to educate them and remind them of the normal ways your credit union would reach out.
First of all, education. Your members can’t guard against a threat they don’t know exists. With Financial Literacy Month coming up in April, now is the perfect time to consider hosting a webinar, sending out a flyer, or posting on social media to make members aware and offer some examples like the ones above.
If they encounter one of these URLs, educate them on recognizing a fake from the real thing because, despite appearances, there are a few ways to tell that a web address using Cyrillic letters is fake. First, instead of clicking on the link on their phone, members should copy and paste the given address into a trusted web browser (remembering to not actually go to the site). Most browsers limit what kinds of characters can be put in a URL (i.e., Cyrillic letters), so if the web address contains any, it won’t work. For other browsers, these scam URLs will change into the actual address when put into a browser. So the fake “amazon.com” will turn into the scammer’s real web address, whatever that may be.
If they’re still unsure, members should go to their browser and type in their credit union web address by hand or follow a previously made bookmark. Alternatively, they can call or reach out to the credit union directly if they want to be entirely sure.
Furthermore, let your members know when and how you will communicate with them. What would you’re credit union never ask for in a text message? If you’re not in the habit of ever sending members text messages, remind them of that as well! That way if they ever receive a text from the credit union, they’ll know right away it’s fake.
Education is key
As scammers learn new methods and seek out new ways to con your members out of their money, credit unions should be working to inform their members of the latest tricks and protect them from bad actors.