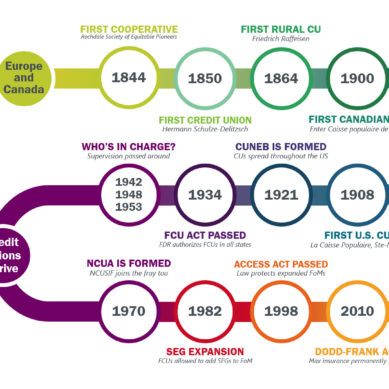
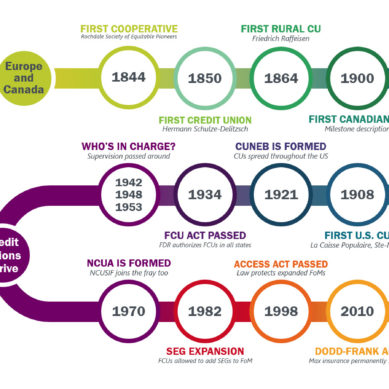
We all hopefully know the basics of cyber safety on the internet: don’t share your password with anyone, don’t leave your device unlocked, don’t click on ads, watch out for scams and phishing attacks, and no, that’s not a real Nigerian prince asking you for money. We’ve heard these all a thousand times and often give ourselves a nice pat on the back for staying cybersafe. But there may be more discrete cyberthreats to your credit union and your members that are slipping through the cracks and going unnoticed–and they’re not coming from suspicious emails.
The flaws in FinTech
I’ve talked quite a bit recently about the rise of FinTechs, the advantages, and what we can learn from these new companies, but the picture is not quite so perfect. Here’s the problem with FinTech: it takes very little for these apps to access all of your members’ online banking information—accounts, cards, spending habits, etc.—all they require is your members to log in to their accounts via the app. If members provide FinTechs with that information only for the FinTech to be a victim of a cyber attack, your members account information will all be vulnerable. And not just their accounts with you, but any account they may have linked to the FinTech.
Long-standing, trusted FinTechs might not be as much of a concern, but new FinTechs are often looking for funding and support and cannot afford to spend as much money on security as other financial institutions. According to Nominet, only 32% of FinTechs, when asked what tech they were planning to buy-in, said cybersecurity.
“FinTech firms are digital natives, born in the cloud,” said Stuart Reed of Nominet Cybersecurity. “They thrive on agile development, innovation, and time-to-market…Unfortunately, this means security is sometimes side-lined.” Cybercriminals know this and will often direct their attacks at such FinTechs, looking for weaknesses in their defenses.
This has become especially relevant in recent years, namely 2020, where the Coronavirus pandemic pushed millions of users to find new online banking methods. During this time, FinTechs saw growth of 50-100% and while that sounds like a great thing, all that growth can prove difficult to keep up with. A drastic increase in users means a drastic increase in the amount of data the FinTech is responsible for, and as they scramble to find ways to maintain and house that data, they potentially leave themselves open for cyberthreats.
Credit unions should be carefully reviewing the security measures for each FinTech they choose to do business with, along with finding ways to educate their members on the risks. Even if your credit union chooses not to work with a FinTech because of security issues, there are hundreds of new finance apps and tools that request access to your members’ private banking information making them potentially vulnerable to attacks, especially if they aren’t reviewing these apps before using.
The risk with vendors
This one goes hand in hand with the previous one (as you’ll see with our example), but it’s important to note that vendors, even outside of FinTechs, can cause cybersecurity incidents. Anytime you bring a third-party vendor into your operations, you have an increased risk of cyberthreats. When you conduct business with vendors, you share private information and data. Should one of you experience a cyberattack or threat, the other would also be put at risk. Meaning, if a vendor’s security system is lacking, your security system is lacking.
According to cybersecurity company Black Kite, even one vendor with holes in their defenses could lead to huge losses for the credit union. They note that “the financial impact of an attack on just one vendor could exceed $1 million for large credit unions and $300,000 for small credit unions.”
FinTech company Dave, for example, experienced a data breach in July 2020 as a result of a cybersecurity incident with one of their third-party vendors, Waydev. The stolen information included customer names, emails, birth dates, physical addresses, hashed passwords, phone numbers, gender, profile picture, application preferences and encrypted Social Security numbers. In total, over 7.5 millions users were affected and the company faced a class-action lawsuit.
That’s not to say that you should shy away from partnering with vendors, but it is essential to thoroughly review all vendors and require SOC reports (if you’re not sure what that is, we’ve got you covered) to track their security measures and controls. Don’t assume that just because a security breach came from a vendor and not the credit union itself that the credit union won’t face losses and repercussions.
The fall of CAPTCHA
Let’s be honest, no one likes CAPTCHA (or its newer version, reCAPTCHA). Clicking every square with a traffic light in it feels like a useless hurdle and can be very frustrating when you—a human—are genuinely struggling to figure out if the tiny right corner of the traffic light crossing into the next box means you should click it.
Not only is this system frustrating, but it does very little in the way of security. When CAPTCHA was first introduced back in 2000, it was a very effective security system that was quick for humans to solve and nearly impossible for bots. Humans simply entered a few numbers or a short word and they were in, whereas bots were left scratching their heads. But now bots have cracked the code, and in response, CAPTCHA has upped its game in a way that has completely failed in its intent. It created a method that has made the system harder for real humans and simple for bots. In fact, you’ll sooner lose an authentic user who is struggling to figure out the solution than keep out a bot, thanks to CAPTCHA solvers.
Sure, on their own bots might not be able to crack the “I am human” code, but there are easy ways around that. Solving a captcha doesn’t just magically let you in the door, it simply provides your computer with a “token” or code, which is then used to access the site. Bots can get around this by sending a copy of the captcha to third-party companies that are paid to solve the captchas. The company will solve the puzzle, retrieve the token, and send that information back to the bot, which they then paste into the site for access. It’s all done through one IP address, and gets around your “security” in around a minute.
This isn’t a rare occurrence either. There are hundreds of these puzzle-solving companies that work for free or charge two cents per puzzle. They have employees working 24/7 with little pay all for the sake of getting bots around your CAPTCHA puzzles. Given these glaring security issues for CAPTCHA and the growth for these puzzle-solving companies, CAPTCHA will either have to change its system again (adding to user frustration) or accept that bots will be able to circumvent the security measure. Aside from providing a false sense of security, the captcha simply creates friction to the user experience, so consider carefully if it’s worth having on your site. Chances are, you could easily do without it.
Find the right balance
Now more than ever, cybersecurity is essential to your credit union operations. If you’re not staying vigilant, things will slip through the cracks. Good cybersecurity also requires checking every weakness to make sure hackers and bots can’t get into your system. However, you have to balance that with user experience, making sure your security systems are effective without being overly frustrating and complicated for the sake of your members. When was the last time you reviewed your cybersecurity measures?