The RSA Conference is the largest cybersecurity conference in the United States. Approximately 45,000 people attend RSA each year. CU*Answers attends each year to learn the latest trends in cybersecurity technology, attack vectors, and compliance. In this series, we summarize what we learned to help our network remain current regarding cybersecurity events and report confidently to their boards, members, and examiners. This article discusses how and why email phishing remains the King of All Scams, and thoughts on how to protect your own organization from this crime.
“Phishing” is unsolicited emails purportedly from a legitimate source requesting personal, financial, and/or login credentials. The FBI’s Internet Crime Center reports over 25,000 phishing attacks a year, and estimates the number of unreported attacks to be several times this number. “Spear phishing,” or specifically targeted emails to particular individuals, are even more dangerous to organizations than general phishing attack campaigns, and more lucrative to the criminal organizations.
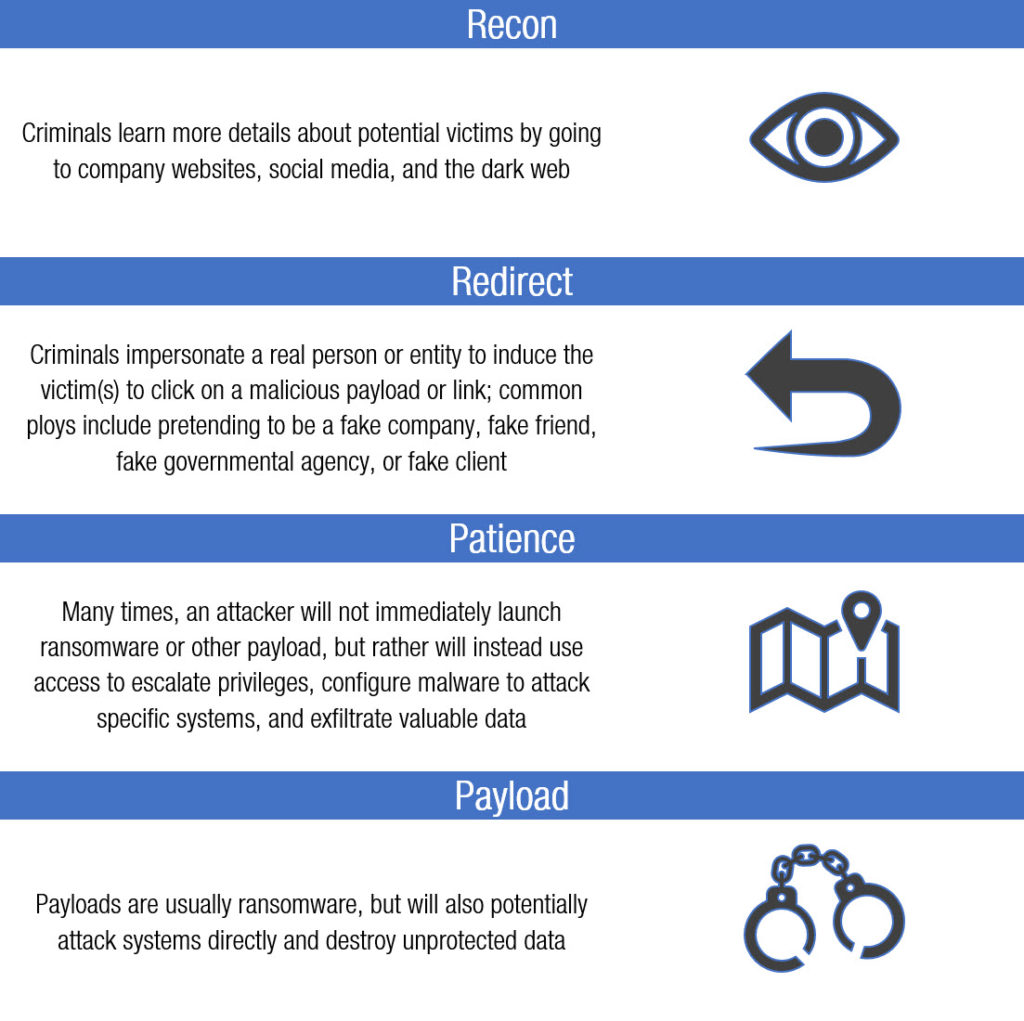
The elements of a sophisticated phishing conspiracy
A key indictment against the alleged North Korean hacker in the Sony Pictures hack (United States v. Hyok) and affidavit alleges the key elements to a sophisticated criminal phishing conspiracy are:
Reconnaissance. These attackers gathered significant personal and professional information about their victims including the “of websites that specialize in locating email accounts associated with specific domains and companies, and the subjects have registered for business records search services that offer career postings, business searches, and marketing services.”
Redirection. The attackers would intercept legitimate emails and copy them, but replacing “hyperlinks in the legitimate email with hyperlinks that would re-direct potential victims to infrastructure under the subjects’ control, presumably in order to deliver a payload of malware to the victims’ computers.”
Patience. The attackers compromised Sony in September 2014 but waited until November of 2014 to make their presence known. In the interim, the attackers were exfiltrating data they would later use to blackmail Sony. Attackers spent time escalating privileges in order to gain as much access and information as possible.
Payload. The particular malware used in the Sony attack was “Destover.” Destover had three primary functions: “(1) it contained a “dropper” mechanism to spread the malicious service from the network servers onto the host computers on the network; (2) it contained a “wiper” to overwrite or erase system executables or program files—rendering infected computers inoperable; and (3) it used a web-server to display the “Hacked By #GOP” pop-up window … and to play a .wav file which had the sound of approximately six gunshots and a scream.” This payload was customized to specifically attack Sony computers and hardware, based on the reconnaissance of Sony’s network.
Common Phishing Methodology
This attack was wildly disruptive to Sony operations. Sony suffered the leak of unreleased films and scripts, employee salaries, company passwords and other sensitive, IT-focused information. Data was wiped from hardware. In addition, Sony employees were threatened with personal and physical harm by the attackers.
In addition, these same actors have been credibly accused of attacking Bangladesh Bank in 2016, resulting in the heist of some eighty million dollars, and the worldwide WannaCry ransomware attack in 2017. These attacks followed the same process as the Sony attack, namely phishing attacks that introduced malware or ransomware into the victim’s network. The relative ease of phishing and the disproportionate size of the rewards means phishing will likely only intensify in prevalence for the foreseeable future. For example, Microsoft reported that phishing attacks on its Office and Outlook products increased by 250% in 2018.
All organizations should take precautions against malicious phishing of their employees. While no solution is foolproof, there are several defenses to phishing that are helpful to minimizing the likelihood and impact of a phishing attack.
Phishing defense mechanisms
Employee training. Rigorously train employees to detect phishing emails. Ensure employees never enter credentials on unfamiliar websites. Do not punish employees who report they made a mistake and fell for a phishing email, and only punish those employees who do not report the attack. Accept that your employees will be phished and will occasionally fall for the scheme. Having employees report and providing key awareness to your IT personnel can be the difference in stopping an attacker’s ability to reconnaissance the network and escalate privileges. Send out alerts to all staff when a phishing email is discovered. Advise staff as to common lures used in phishing attacks, such as fake billing or invoices, phony executive demands, false account lockouts, and impersonation of friends/family/co-workers/government.
Label Email from Outside Sources. Warn all employees when an email arrives from an external source. This can reduce the incidents of employees falling for a phishing attack that appears to come from a legitimate internal source.
Web Filtering. Web filtering software that can block an employee from following a link to a malicious site can save an employee from disrupting operations and can also provide a learning experience for an employee that has fallen for a phishing scam.
Do Not Operate as a Local Administrator. All users, even administrators, should operate their computers as a standard user and not as a local or domain administrator. Operating as a standard unprivileged user can slow or stop some phishing attacks because it can prevent malware from being installed on the computer or bad actors from instantly having administrator access if the PC is compromised remotely.
Set Restrictive Permissions on Files and Folders. Use standard operating system controls to restrict the ability to modify or delete files and folders to only those users who need that ability. This will prevent cryptoware/ransomware from encrypting or destroying the organization’s files and folders.
Store Backup Files Offline or as Read Only. This will protect backups from being damaged or destroyed by a cryptoware/ransomware attack that is able to find backup archives on the network.
Update Anti-Virus Software Continuously. Anti-Virus software can help stop the malware installation attempt and stop the spread of malware within the network.
Review Access Controls. Reduce the number of employees that have access to critical systems and be sure these employees are regularly trained to detect phishing attacks.
Penetration Testing. Conduct regular penetration testing and scans of your network to detect vulnerabilities. Be sure employees are tested against social engineering ploys.
Incident Response. Be sure that the incident response plan of the organization includes communications with the public, and includes procedures for forensics in the event a serious phishing compromise occurs.
All organizations should make anti-phishing controls their number one cybersecurity priority for the foreseeable future. There is no evidence that criminal organizations will slow down the number of phishing attacks anytime soon; in fact, the odds are likely that phishing attacks will continue to increase. The next installment in this series will discuss in more detail how foreign criminal gangs are organized, and insight into how these crime rings operate on a daily basis.